
Using John the Ripper to Crack MD5 Hashes
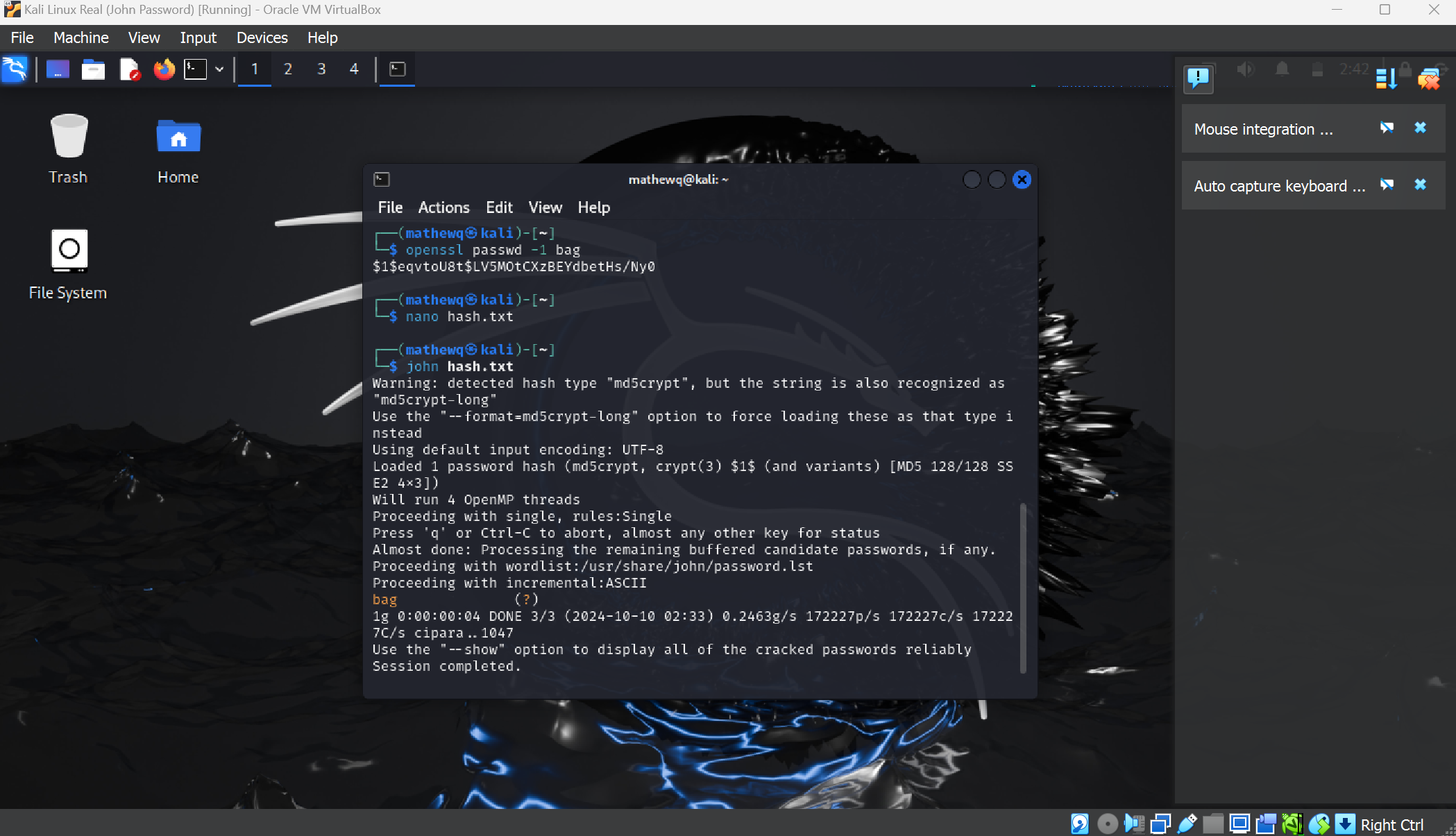
In this project I used serval security applications to achieve the end goal of learning how John the Ripper or John works. I started by powering on my virtual machine to get more familiar with the Kali Linux operating system and what applications are included in Kali Linux. After starting up the program I used the command line to first hash the word bag (the password I will decrypt later) using the MD5 hash. Then I copied the output hash and pasted the string of random characters into the text file using the text editor. Following that step, I used commands from John to evaluate the hash and after about 5 seconds it provided me with the word bag. I learned a lot from this simple project. It reenforced the idea of creating strong passwords when securing and sensitive information. I tried the same process with a hash thisismypassword and John the Ripper could not crack the hash in a reasonable amount of time. Asking chatGPT how long it would take to crack the 16 character hash encrypted by MD5 it claims it would take 1.4 million years depending on the computer if performing a brute attack. My next step in this project is learning how to use a dictionary to perform a dictionary attack to allow John the Ripper to be more efficient and crack stronger hashes.